Introduction
Welcome to the world of Open-Source Intelligence (OSINT), where publicly accessible information becomes a powerful tool for gathering insights and making informed decisions. OSINT is the practice of collecting, analyzing, and disseminating information from sources that are freely available to the public. This can include data from the internet, traditional media, academic publications, and even physical sources like maps and satellite imagery.
In today's digital age, OSINT has become an indispensable asset for various sectors, including cybersecurity, business, journalism, and research. It allows individuals and organizations to gather valuable information without breaching privacy or intellectual property laws. Whether you're a cybersecurity professional, a business analyst, or simply someone curious about the digital world, OSINT provides a wealth of data that can be leveraged to gain a competitive edge or enhance security measures.
In this article, we'll delve into the basics of OSINT, explore its various applications, and discuss the tools and techniques used to gather and analyze this information. We'll also examine how OSINT is used in real-world scenarios, from reconnaissance in cybersecurity to competitive intelligence in business. By the end of this journey, you'll have a comprehensive understanding of OSINT and how it can be a powerful ally in your professional and personal endeavors.
Lab Questions and Answers: 1.1 Core Concepts
1. What does OSINT stand for?
A. Open-Source Internal Networking
B. Open-Source Internal Negotiations
C. Operational Security Internet Navigation
D. Open-Source Intelligence
E. Operational Security Inside Network Topologies
F. Operational Security Intelligence
Answer: D
2. OSINT can best be described as:
A. Collection and analysis of information from public resources to develops insights about people and things.
B. Internation negotiations
C. Being transparent about the sources of your information
D. Conducting undercover physical surveillance
Answer: A
3. Which of the following is NOT a common OSINT resource?
A. Company Website
B. Web Archives
C. Private emails
Answer: C
Lab Questions and Answers: 1.2 Guided Exercise
1. Based on job postings, RektSystems is likely using which version of phpMyAdmin? Hint: *.*.*
Answer: 4.8.1
2. You’ll notice a reference to a Xerox machine used to generate this PDF. You have a specific identifier that you can use to search for vulnerabilities. Perform a Google search for the CVE associated with the vulnerable Xerox device. What is the CVE of that vulnerability?
Answer: CVE-2019-10881
3. Using the country code discovered (e.g., US or CA) in the response to your WHOIS query, determine in which country the registrant (rekt.systems) is located.
Answer: Iceland
4. What is the flag found after successfully redeeming the token you discovered?
Answer: {T:STNG}
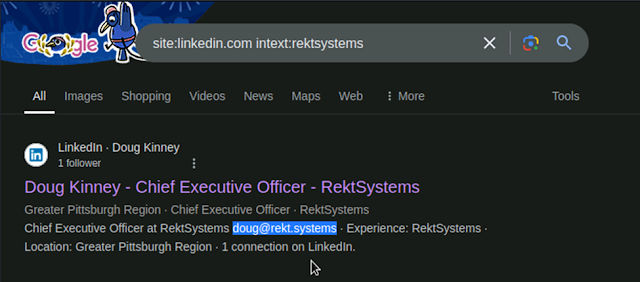
5. What is the email address of the CEO of Rekt Systems?
Answer: doug@rekt.systems
Lab Questions and Answers: 1.3 Challenge Exercise
1. What additional subdomain did you discover (aside from login.rekt.systems and rekt.systems)?
Answer: tstng.rekt.systems
2. What file was previously in robots.txt that was removed?
Answer: login.html
3. What is the name of the island on which this picture was taken?
Answer: rick roll island
Conclusion
In this OSINT Hands-on Lab, you've successfully applied various techniques to gather and analyze information about a target, RektSystems. You've learned how to use CTI platforms, web archives, and metadata analysis tools to gather valuable information without actively engaging with the target.
By completing this lab, you've gained a solid understanding of OSINT principles and techniques and are now ready to apply them in your own investigations. Remember to always follow best practices and respect the law and your client's scope. With practice and experience, you'll become proficient in using OSINT to gather valuable information and stay one step ahead of your targets.