Introduction
In this lab, you'll learn the fundamentals of log analysis, a crucial skill for security professionals, IT professionals, and anyone interested in understanding the inner workings of computer systems. Log analysis is the process of examining log files to identify patterns, trends, and anomalies that can help you troubleshoot issues, detect security threats, and optimize system performance.
What is a Log?
A log is a record of events that occur on a computer system, including user interactions, system errors, and security incidents. Logs can be generated by various sources, including operating systems, applications, and network devices. In this lab, you'll learn how to analyze logs to extract valuable information and make informed decisions.
Objectives
By the end of this lab, you'll be able to:
Define and describe computer logs
Identify and describe the key components of a log record
View and interpret text log records
Conduct simple searches of text logs using the command line
Understand the basics of log analysis and its applications in security and IT
What to Expect
In this lab, you'll work with sample log files and learn how to analyze them using various tools and techniques. You'll also learn about the different types of logs, log formats, and log analysis tools. By the end of this lab, you'll have a solid understanding of log analysis and be able to apply your skills in real-world scenarios.
Let's Get Started
In the next section, we'll dive into the world of log analysis and explore the different types of logs, log formats, and log analysis tools. You'll learn how to view and interpret text log records, conduct simple searches, and understand the basics of log analysis.
Lab Questions and Answers: 1.1 Core Concepts
1. A computer log is best defined as:
A. Binary data bounded by specific delimiters.
B. A specialized type of database.
C. A record of the events occurring within an organization’s systems and networks.
D. Event-specific metadata.
Answer: C
2. In the context of a computer log, a field is best defined as:
A. A single entry in a log.
B. A single, discrete element of data in a record.
C. Event-specific metadata.
D. A character used to separate records.
Answer: B
3. Which of the following are elements commonly found in log records?
(select all that apply)
A. Date
B. Event Type
C. Binary
D. Search Expressions
E. Success or Failure
Answer: A, B, E
4. The command <egrep -i “failure" host.log> will:
A. Conduct a search for the literal term “failure" (case sensitive) in the file “host.log”
B. Conduct a search for the literal term “failure" regardless of case in the file “host.log”
C. Conduct a search for the literal term “failure" regardless of case in all files in the present working directory that end with a ".log" file extension.
D. Conduct a search for the literal term “failure” (case sensitive) in all files in the present working directory that end with a ".log" file extension.
Answer: B
Lab Questions and Answers: 1.2 Guided Exercise
1. What is the time stamp of the earliest record in the file web.log.2?
Answer: 00:13:00
2. Which file in the Practice directory has the most lines?
3. What is the username of the account used for VPN authentications with the same source IP address as the "test" account(s)?
4. Which of the following usernames do not appear in the practice.log.2 file. (Hint: This will require running additional searches.)
(select all that apply)
A. vpn_user
B. vpn_1234
C. guest_vpn
D. secure_vpn
Lab Questions and Answers: 1.3 Challenge Exercise
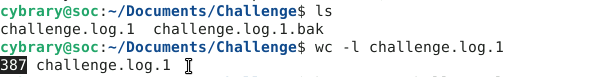
1. How many lines are contained in the file challenge.log.1?
2. What is the timezone indicated in the header row of challenge.log.1?
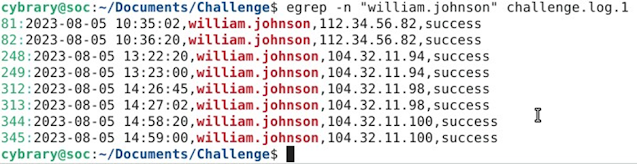
3. How many different IP addresses can be found in login records that contain the username "william.johnson"?
4. Another username was observed authenticating from the same IP address as one of those associated with the "william.johnson"?
Answer: emily.jones
Conclusion
In this lab, we explored the basics of log analysis and practiced using various commands to profile and search log files. We gained hands-on experience with log analysis and developed a basic understanding of the skills and techniques required to analyze log files. By completing this lab, we have taken the first step in developing our log analysis skills and are now better equipped to analyze log files and extract valuable information from them.
With practice and experience, we can continue to develop our skills and become proficient in log analysis. Log analysis is a critical skill for security professionals and IT professionals, and it requires attention to detail, critical thinking, and problem-solving skills. By applying log analysis skills to real-world scenarios and case studies, we can gain practical experience and improve our skills.