Introduction
In today's rapidly evolving digital landscape, safeguarding an organization's information assets is paramount. One of the critical tools in a cybersecurity professional's arsenal is SIEM, which stands for Security Incident and Event Management. Unlike traditional log aggregation systems, a SIEM goes beyond merely collecting logs; it analyzes and correlates them to identify potential security incidents. This proactive approach allows security teams to visualize and respond to threats across the entire enterprise efficiently.
In this hands-on lab, we will delve into the capabilities of Wazuh, a popular open-source SIEM solution. Wazuh stands out by integrating extended detection and response (XDR) functionalities, providing a comprehensive security monitoring solution. Built on OSSEC and Elastic Stack, Wazuh offers robust features such as intrusion detection, file integrity monitoring, compliance checks, vulnerability detection, and more.
Throughout this lab, you will gain practical experience with Wazuh's core components, including its agents, server, indexer, and dashboard. You will learn how to navigate the Security Events Dashboard, utilize Apache Lucene query syntax for efficient data searching, and interpret various security alerts and visualizations. Additionally, you will simulate an attack scenario to understand how Wazuh detects and logs such events, providing a real-world context to the theoretical knowledge.
By the end of this lab, you will have a solid understanding of how Wazuh can be leveraged to enhance your organization's security posture, making it an invaluable tool in the fight against cyber threats.
Lab Questions and Answers: 1.1 Core Concepts
1. What does SIEM stand for?
A. Security Insight and Enterprise Management
B. Security Incident and Enterprise Management
C. Security Incident and Event Management
D. Security Insight and Event Management
Answer: C
2. What are some popular SIEMs?
(select all that apply)
A. Splunk
B. OpenVAS
C. QRadar
D. Elastic Stack
E. Nikto
Answer: A, C, D
3. What are the primary components of the Wazuh SIEM?
(select all that apply)
A. Server
B. Filebeat
C. Indexer
D. Agent
E. Dashboard
Answer: A, C, D, E
4. Which of the following are SIEMs used for?
(select all that apply)
A. Aggregating logs
B. Recovering data
C. Normalizing data
D. Patching vulnerabilities
E. Visualizing security events
F. Searching for IOCs
Answer: A, C, E, F
Lab Questions and Answers: 1.2 Guided Exercise
1. What are the primary fields in the Add Filter tool?
A. Field, Operator, Value
B. Field, Designation, Value
C. Value, Operator, Number
D. Value, Designation, Date
Answer: A
2. How many security events remain after filtering out the host-based anomaly detection (rootcheck) events?
Answer: 10
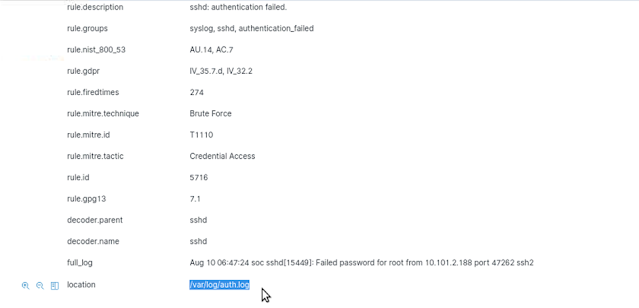
3. What is the Rule ID value for the level 5 "sshd: authentication failed" alerts?
Answer: 5716
4. What is the location of the log file where the brute force events were recorded?
Answer: /var/log/auth.log
Lab Questions and Answers: 1.3 Challenge Exercise
1. What is the Rule ID for the “sshd: Attempt to login using a non-existent user” alerts?
Answer: 5710
Hint: Use this command to find --> rule.description:"sshd: Attempt to login using a non-existent user"
2. What was the total number of login attempts for a non-existent user?
Answer: 86
Hint: Click Bruteforce part of the piechart or use filter to filter out only bruteforce attacks.
> rule.mitre.technique: Brute Force
Conclusion:
This hands-on lab provided practical experience with the Wazuh SIEM system, focusing on essential skills for security professionals. You learned to navigate the Wazuh interface, manipulate date ranges, and apply filters to isolate relevant security events. By simulating an attack, you gained firsthand experience in using SIEM tools to detect and analyze potential security breaches.
The lab emphasized the importance of reducing noise in log data and identifying critical security events. You practiced interpreting both individual log entries and aggregated data, understanding their roles in comprehending the full scope of an attack. These skills are crucial for effective monitoring and protection of network environments.
Overall, this exercise demonstrated the power of SIEM tools in cybersecurity and underscored the need for continual learning and practice in log analysis and incident response.