Welcome to this lab walkthrough on access control basics. In this lab, we will explore the concepts of access control and how to implement it in a Windows environment. We will cover the different access control models, including Mandatory Access Control (MAC), Discretionary Access Control (DAC), and Role-Based Access Control (RBAC). We will also examine how to use Windows permissions to control access to files and folders, and how to use the icacls command-line tool to manage and verify access control lists (ACLs).
Throughout this lab, we will work through a series of exercises that will help you understand how to apply access control in a Windows environment. We will start by exploring the basics of access control and then move on to more advanced topics, such as inheritance and advanced permissions.
By the end of this lab, you will have a solid understanding of access control in Windows and how to use it to protect sensitive resources. Let's get started.
Lab Questions and Answers: 1.1 Core Concepts
1. Access control is best defined as:
A. The process by which a subject proves their asserted identity.
B. The process of authorizing a subject to access an object.
C. The process of giving permission or authority.
D. The process by which an object receives the same permissions as its parent object.
Answer: B
2. Which of the following access control models would be most appropriate to aligning permissions according to functional groups?
A. Mandatory Access Control (MAC)
B. Discretionary Access Control (DAC)
C. Role-Based Access Control (RBAC)
Answer: C
3. Which of the following access control models would be most appropriate for a military setting?
A. Mandatory Access Control (MAC)
B. Discretionary Access Control (DAC)
C. Role-Based Access Control (RBAC)
Answer: A
4. Which of the following access control models assigns permissions directly to subjects?
A. Mandatory Access Control (MAC)
B. Discretionary Access Control (DAC)
C. Role-Based Access Control (RBAC)
Answer: B
Lab Questions and Answers: 1.2 Guided Exercise
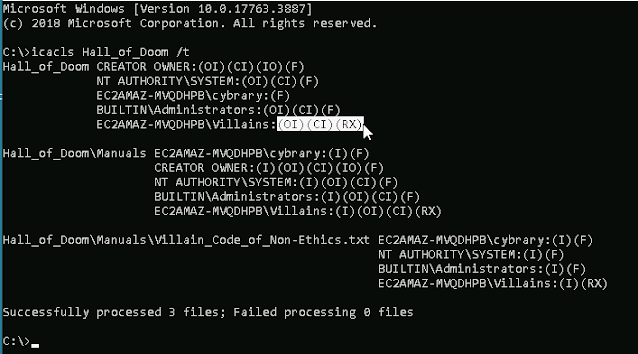
1. After adding the Villains group to the Hall_of_Doom folder, what permissions does the Villains group have for the Hall_of_Doom folder (in icacls format)?
Answer: (OI)(CI)(RX)
2. In addition to lex.luthor, what is the name of the other user account in the Leaders group?
Answer: clark.kent
3. At the end of the exercise, which of the following permissions does the lex.luthor account not have effective access for on the Leadership folder?
(select all that apply)
A. Traverse folder / execute file
B. Delete subfolders and files
C. Delete
D. Write attributes
Answer: B
4. At the end of the exercise, which of the following permissions does the lex.luthor account not have effective access for on the C:\ drive?
(select all that apply)
A. Traverse folder / execute file
B. Delete subfolders and files
C. Delete
D. Write attributes
Answer: B, C, D
Lab Questions and Answers: 1.3 Challenge Exercise
1. What user was added to the Leaders group?
Answer: bizarro
2. What group was granted access to the Hall_of_Doom folder?
Answer: Cheaters
3. How many users are in the group above?
Answer: 3
4. What undesired permission does this group have on the Hall_of_Doom folder?
Answer: Full
Conclusion
In this lab, we explored Windows access control and learned how to manage permissions on files and folders using the icacls command and the Security tab. We added users and groups to the access control list (ACL) and assigned permissions and used the Effective Access feature to view effective permissions. By completing this lab, you should now have a good understanding of how to manage access control in Windows.